So you think you've been hacked by a sophisticated hacking group, what next?
Advice for people who suspect they or/and their friends/family are being persistently hacked on every platform
This is a bit different from my usual content, but I often get approached by people who are desperate for help because they strongly suspect they are a victim of persistent hacking attempts, usually from gangs. So this is a post for them that I can hopefully share to help alleviate their fears and stress. If you’re expecting how to hack content this is not the post for you.
How the hackers get in
Let’s start out by first talking about how hackers get into your accounts. The vast majority of hacks are credential stuffing attacks or phishing and other types of social engineering. If you run a business the attacks are slightly different, so we’ll talk about that in another post.
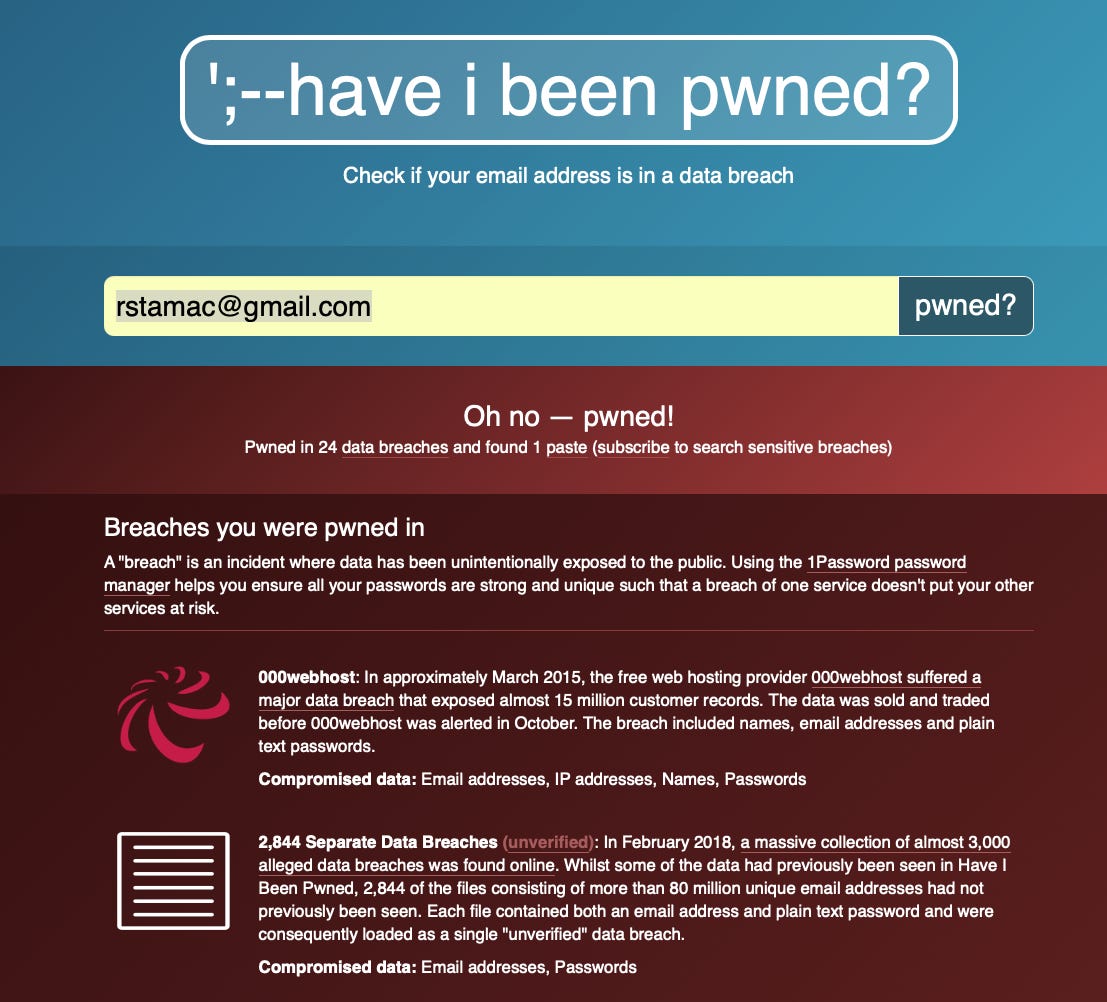
A credential stuffing attack is where hacker A will hack a platform, and resell the usernames/passwords from that platform to hacker B. Hacker B then tries to use that username/password combo on another website, hacker B might get this data several months or even years after hacker A actually hacks the platform. This is why it’s so important to use a password manager like 1Password, you can easily use unique passwords for every service, so a password can’t be reused on another website. This kind of attack is extremely common, even I have been a victim to this type of attack because I reused a password many years ago. You can check if your email appears on a breach using the free website haveibeenpwned.com, you can do the same for your passwords, don’t worry this is completely safe.
The next common breach is phishing and other types of social engineering. Social engineering covers psychological and social techniques that enable an attacker to gain some information from you, it’s psychological manipulation at its core. You’ve probably seen this attack before, whether it’s a Nigerian Prince scam, or someone claiming to be your child with a new number. You should verify anyone who claims to be from an organisation by asking them to answer a question only the genuine company would have the answer to, for example if someone calls you from Amazon, ask them to confirm the date or number of another order. Some pieces of information you can ask for: billing date, order numbers, a family member’s name.
Phishing is similar, but instead of you talking to a human, the attacker will setup a genuine looking website, even the link will look the same, but in reality it is completely fake, like a house with only the front facade, and will harvest your username and passwords. You can usually tell if you’ve been a victim of this if you login to an account, and the page refreshes and you’re still on the login page. Don’t trust links to pages that ask you to login, instead type in the URL and navigate to the page yourself.

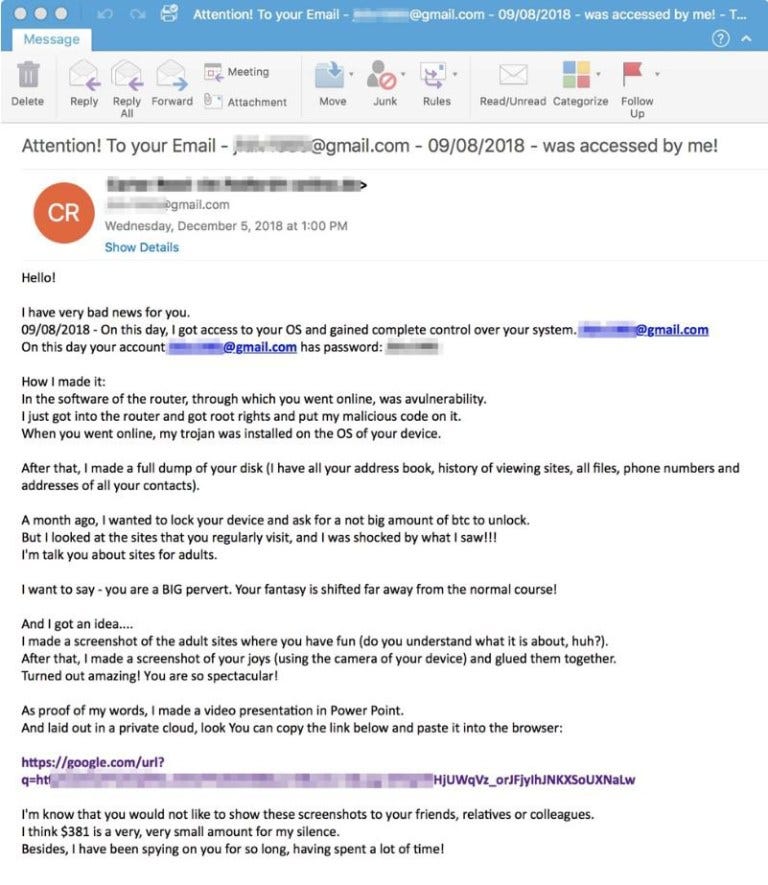
Finally you might see blackmail, this is another type of social engineering. The email claims they have hacked your account and installed malware onto your system. They usually go on to claim when they did so that they were able to see your history and webcam and have been spying on you for some time. They threaten to release videos to your friends, family or co-workers, unless you pay them a ransom in bitcoin. In the example below you can see that they include an email and password to “verify” (this is usually taken from a historical data breach like credential stuffing), and a link to their presentation they’ll send onwards (this is usually a phishing link).
Motivations
The main motivator for attackers is money, either you to directly send them money, to hack a platform that has your money (online banking, PayPal etc) so they can send money to themselves, for you to install a bitcoin miner on your device that they can use to generate money, or for an account that has resell value (like steam accounts). Most hackers do not care about anything beyond this, including ruining your life, unless you’ll pay a blackmail. It would be very unusual for an attacker to target you for another reason.
If you do have a presence online, for example you’re a celebrity you might be at increased risk, but the attackers still want to make money. For example security company Mandiant, which was bought by Google for $5.4b in 2022, had their twitter account breached. This is a very valuable account, followed by journalists, security professionals, and CEOs, and it’s just funny that a security company got breached. What happened next? Well it changed it’s name, handle and brand identity to Phantom, and shared a phishing link that targets crypto wallets. There was a potential for a slow, sophisticated attack, but why spend time on that when instead you can go for the easy crypto wallet drainer.
This is true for a lot of scams, we have Martin Lewis a UK based public figure who runs a money advice website, who has been the star of a deepfake video without his knowledge promoting an Elon Musk “investment”. If you’re a business you might have been the victim of Ransomware, where your networks are hacked and files are encrypted by an attacker, scrambling all the data and making the computer unusable, unless you pay a “small” fee to get the code to unscramble them. I can’t stress this enough: Hackers want your money, they don’t want you, you’re the annoying bit they have to manage between them and getting your money.
0days and 0clicks
Sometimes people tell me they think they’ve been hacked through what are called 0click type exploits. These are exploits that target your phone or computers operating systems and do not require you (the victim) to do anything. Usually these are RCEs or Remote Code Execution type vulnerabilities, these are vulnerabilities that allow an attacker to run arbitrary code on your computer. The best way to avoid these vulnerabilities is to always have your phone and other software on the most updated version. However some people tell me they are worried about a 0day, a 0day vulnerability is any vulnerability that the make of the software doesn’t know about, so there is no fix available yet. To give you an idea of how valuable these are, a hacker like me can sell an RCE 0day to governments in North America or Europe through Zerodium at $1m for windows, or $2.5m for android. To see one of these in the wild, without a fix, is rare and warrants an immediate patch . If you look at the article linked above, this was found by researchers examining the spyware application “Pegasus”.
Pegasus is usually dubbed as a ‘mercenary’ application. It is a piece of spyware that uses a 0click exploit to completely infect a device, downloading emails, messages, files etc... While NSO Group, the creators of Pegasus, claim it is only sold to governments to surveil terrorist groups or criminal gangs. Pegasus has been often found on devices belonging to those critical of their government. The exploits Pegasus use are extremely valuable, and the cost for 10 iPhones is $650,000, plus a $500,000 install fee. Unless you are a journalists or activist critical of your countries government you are not worth the cost to hack using these sophisticated techniques. Individuals who believe they are being targeted (again this is activists, journalists, political figures who are critical of their government, being targeted by their government) or diplomats working in a foreign country, if you are a regular person you will not be targeted by this spyware) can arrange for their devices to be forensically examined and the underlying vulnerabilities are then sent to their makers, e.g. Apple for iOS to be fixed.
I want to stress this again: If your prime minister or president or head of the ruling political party doesn’t know your name, you are not going to be targeted by Pegasus.
Protecting yourself
Okay so what can you do to protect yourself? So here are my tips, I’ve ordered these starting with the most helpful, general things you can do, as you go down the list they are more extreme. As you go down the list you are going to be more restrictive, that is the nature of the trade off. I do know that people worry and perhaps the extreme measures will make them feel safe.
The first thing you should do if this is worrying you is speak to a healthcare professional, while it is normal to feel spooked after your accounts are hacked most hacks take minutes to resolve with a simple password change. If you find that this worry consumes you, nothing on this list will give you the peace of mind you need. Unless you are the head of the opposition party of your hostile government you are not going to be targeted by sophisticated attacks, and it is my professional opinion that your worries are unfounded.
Are you a hacker with more advice, let me know in the comments!
Reset passwords on compromised accounts - As soon as you get a notification that someone has logged into your account you should reset your password as soon as you can.
Enable 2 factor authentication where possible - 2 factor authentication (2FA) means you use another thing in addition to your password, usually an authentication number. Almost all services allow you to enable 2FA, using a second app like Google Authenticator, Microsoft Authenticator or Authy. These apps use a secret from the service you’re trying to login to and your phone, to generate a short code every few seconds, when you login you input the code as well as your password. Without this code an attacker can’t login. This is how I secure all my accounts.
Use a password manager - A password manager makes it easy to use unique, strong passwords on every website, I use 1Password and the OSX password manager.
Stop pirating - If you’re illegally downloading movies, TV shows, or games you are more likely to download malware alongside or instead of the file you wanted, instead switch to streaming services.
Update your software as soon as an update is available - If you’re worried about more targeted accounts simply updating software as soon as it’s available will ensure you get all the security patches by your manufacturer.
Review account security regularly and delete old accounts - You should review the security of all of your accounts, checking for 2FA, and password security regularly, you may also want to sign up for alerts with HaveIBeenPwned (Notify in the top bar), if you no longer use an account you should fully delete these.
Block adverts - Adverts can often contain malware, sometimes called Malvertising, these often take the form for “YOUR COMPUTER IS INFECTED” adverts on websites, use an adblocker on your platform of choice to to ensure you do not click on these ads accidentally.
Use signal instead of WhatsApp - Signal is a messaging app that you can use instead of WhatsApp, it’s completely free and offers more privacy features such as not sending data back to Facebook.
Use a physical security key - A Yubikey is a physical device that you can use as part of the login process, it’s similar to 2FA but instead of an app or your phone instead it’s a physical thing you must have.
Only download apps from the App Store - Apps on the AppStore have to be checked for security, if they fail they are removed, by only using official, tested applications, you can reduce the chance of being infected with Malware. This is very rare.
Setup a PIN code with your mobile phone provider - If you’re a public figure and concerned about SIM swap attacks, many providers allow you to setup additional security on your SIM card, you should contact your phone provider to learn more as it will be different in every country and with every provider.
Switch to the Apple Ecosystem - iPhones by their nature are more limited than Android phones, while there are intentional breaches of iOS a “Jailbreak” you need to intentionally run the Jailbreak yourself. However the main reason why you’d want to switch is to have the most extreme protection, Lockdown Mode.
Use lockdown mode - Lockdown mode was designed for journalists, activists and targets of government-level surveillance, it will severely limit what you can do with your device by preventing attack vectors, websites will be limited, message attachments blocked, these are common entry points for spyware like Pegasus, preventing infection.








When i suspected my partner was cheating , I really wanted to see his chats and the contents of his mobile phone
but i didnt have his password. I went in search of a hacker and found Aceteam on a site with so many
good reviews about his services so i reached out to him. To my Upmost surprise he successfully hacked
my mans phone and i could read his messages with his ex . He was so shocked when i sent him screenshots of them exchanging
love messages. if you also need a private mobile penetration then send contact : aceteamhackers @ gmail .. com
If you require a hacker for hire services or you want to hack your friend/partners mobile phone to find out what they are up to? do you want access to mails,
whatsapp, tik tok ,facebook, instagram, twitter? do you want change your school grades ,transcripts or enrollment?
remove criminal records. if you do need a hacker for any type of hacking services, send a message to : cyberspace911 @ gmail com